BIOPASS RAT Infects Chinese Gambling Sites

BIOPASS RAT was initially identified immediately after the malware made its debut on a targeted Chinese online gambling website.So far, we only know it is in development and that it's targeting mostly Chinese online browsers, including 2345 Explorer, QQ Browser, 360 Safe Browser, Sogou Explorer, and WeChat.
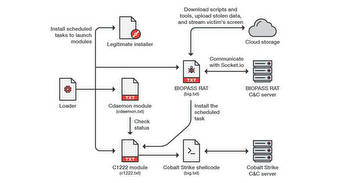
The updated malware can deploy either BIOPASS RAT or Cobalt Strike beacons. Both versions are able to record their victims' screens using OBS Studio.By employing BIOPASS, cybercriminals may easily access a variety of spyware features like live streaming on a cloud service through Real-Time Messaging Protocol (RTMP), as well as connecting with a C2 server via Socket.IO.
Cybercriminals disguise the malware in installer packages that look like real software installers
To carry out the attack hackers use malicious loaders masquerading as genuine installers for popular but outdated applications such as Microsoft Silverlight or Adobe Flash Player. As you probably hinted, the malware loader then acts as a conduit for collecting the next-stage payloads. Malicious JavaScript has also been found hidden inside the websites' online help chat pages whose role is to infect users with malware once they have logged in.
Trend Micro research reads "BIOPASS RAT possesses basic features found in other malware, such as file system assessment, remote desktop access, file exfiltration, and shell command execution," [...] "It also has the ability to compromise the private information of its victims by stealing web browser and instant messaging client data."
The identity of the malicious agent is still unknown. Then again, based on Trend Micro research, the malware strain has similarities with that of TTPs, which is often linked with the Winnti Group.